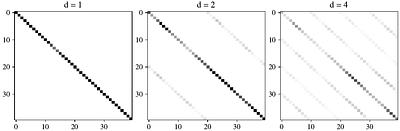
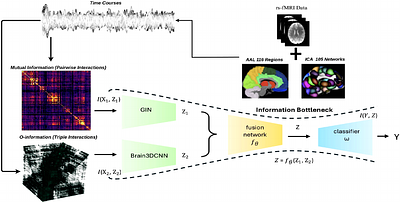
By: Daniel Haider, Vincent Lostanlen, Martin Ehler, Nicki Holighaus, Peter Balazs
Differential Mamba
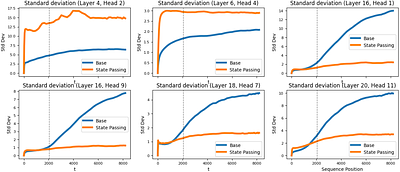
By: Nadav Schneider, Itamar Zimerman, Eliya Nachmani
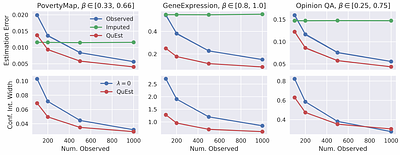
QuEst: Enhancing Estimates of Quantile-Based Distributional Measures Using Model Predictions
By: Zhun Deng, Thomas P Zollo, Benjamin Eyre, Amogh Inamdar, David Madras, Richard Zemel
By: Corrado Rainone, Tim Bakker, Roland Memisevic
By: Lorenzo Braccaioli, Anna Vettoruzzo, Prabhant Singh, Joaquin Vanschoren, Mohamed-Rafik Bouguelia, Nicola Conci
By: Guanhua Zhang, Ricardo Dominguez-Olmedo, Moritz Hardt
By: Konstantin Nikolaou, Sven Krippendorf, Samuel Tovey, Christian Holm
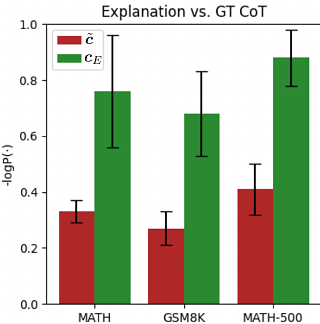
By: Rahul Thomas, Louai Zahran, Erica Choi, Akilesh Potti, Micah Goldblum, Arka Pal
By: Kunyu Zhang, Qiang Li, Shujian Yu
Replicable Distribution Testing
By: Ilias Diakonikolas, Jingyi Gao, Daniel Kane, Sihan Liu, Christopher Ye
By: Thiti Suttaket, Stanley Kok
By: David H. Mguni
By: Yuchen Ma, Dennis Frauen, Jonas Schweisthal, Stefan Feuerriegel
By: Aurko Roy, Timothy Chou, Sai Surya Duvvuri, Sijia Chen, Jiecao Yu, Xiaodong Wang, Manzil Zaheer, Rohan Anil
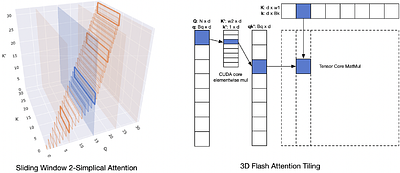
By: Ricardo Buitrago Ruiz, Albert Gu
By: Ruiyang Zhou, Shuozhe Li, Amy Zhang, Liu Leqi
Revisiting Learning Rate Control
By: Micha Henheik, Theresa Eimer, Marius Lindauer