Secure-by-design smart contract based on dataflow implementations
Secure-by-design smart contract based on dataflow implementations
Simone Casale Brunet, Marco Mattavelli
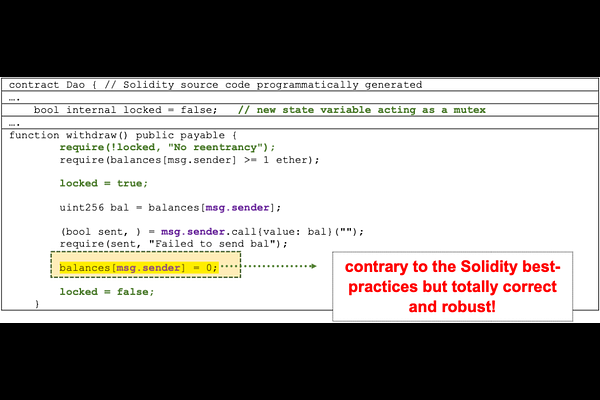
AbstractThis article conducts an extensive examination of the persisting challenges related to smart contract attacks within blockchain networks, with a particular focus on the reentrancy attack. It emphasizes the inherent vulnerabilities embedded in the programming languages commonly employed for smart contract development, particularly within Ethereum Virtual Machine (EVM)-based blockchains. While the concrete example used primarily employs the Solidity programming language, the insights garnered from this study are readily generalizable to a wide array of blockchain architectures. Significantly, this article extends beyond the mere identification of vulnerabilities and ventures into the realm of proactive security measures. It explores the adaptation and adoption of dataflow programming paradigms, employing Domain-Specific Languages (DSLs) to enforce security by design in the context of smart contract development. This forward-looking approach aims to bolster the foundational principles of blockchain security, offering a promising research direction for mitigating the risks associated with smart contract vulnerabilities. The objective of this article is to cater to a diverse audience, ranging from individuals with limited computer science and programming expertise to seasoned experts in the field. It provides a comprehensive and accessible resource for fostering a deeper understanding of the intricate dynamics between blockchain technology and the imperative need for secure smart contract development practices.